Pfsense IPSEC mobile AUTHENTICATE
Good morning,
I have created a mobile ipsec tunnel, it works when I authenticate users with pre-shared keys.
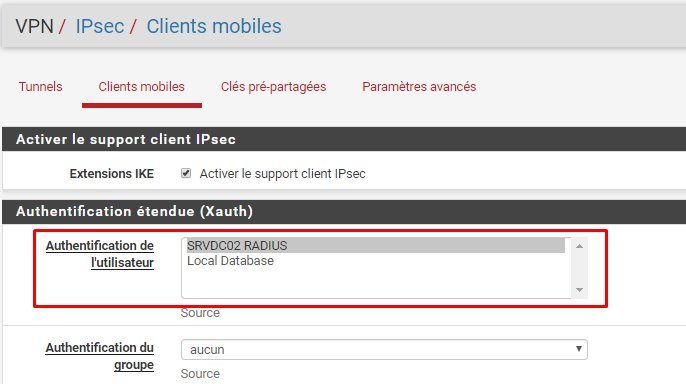
But it is impossible to make them authenticate by radius server "NPS windows server 2016" or "Local Database".
I tested the authentication with "diagnostics --> Authentication" it works.
I looked at Wireshark on the RADIUS server + network capture on the LAN interface of the pfsense where the RADIUS server is located BUT also the IPSEC and NPS logs.
I put all the screenshots at the end.
What I could see with all these tests :
The RADIUS server gets NO requests when a user tries to authenticate. So I have no new NPS log and no frame on wireshark "source pfsense LAN --> destination RADIUS server".
Even when I choose on pfsense in mobile client the radius server for authentication, I still manage to connect with "Pre-shared key" users.
So I think pfsense does not take into account my choice of authentication server.
TUTO that I followed:
https://michaelfirsov.wordpress.com/testing-pfsense-ipsecv2-vpn-with-win ...
https://michaelfirsov.wordpress.com/testing-pfsense-ipsecv2-vpn-with-win ...
If you have any ideas on how to solve the problem or direct me to the solution, that would be very kind of you.
I can give much more information very quickly, if you need it.
IPSEC LOG:
I have created a mobile ipsec tunnel, it works when I authenticate users with pre-shared keys.
But it is impossible to make them authenticate by radius server "NPS windows server 2016" or "Local Database".
I tested the authentication with "diagnostics --> Authentication" it works.
I looked at Wireshark on the RADIUS server + network capture on the LAN interface of the pfsense where the RADIUS server is located BUT also the IPSEC and NPS logs.
I put all the screenshots at the end.
What I could see with all these tests :
The RADIUS server gets NO requests when a user tries to authenticate. So I have no new NPS log and no frame on wireshark "source pfsense LAN --> destination RADIUS server".
Even when I choose on pfsense in mobile client the radius server for authentication, I still manage to connect with "Pre-shared key" users.
So I think pfsense does not take into account my choice of authentication server.
TUTO that I followed:
https://michaelfirsov.wordpress.com/testing-pfsense-ipsecv2-vpn-with-win ...
https://michaelfirsov.wordpress.com/testing-pfsense-ipsecv2-vpn-with-win ...
If you have any ideas on how to solve the problem or direct me to the solution, that would be very kind of you.
I can give much more information very quickly, if you need it.
IPSEC LOG:
Mar 26 17:55:00 charon 13[NET] <2> received packet: from IP PUBLIQUE DU CLIENT[1038] to IP PUBLIQUE WAN PFSENSE[500] (1104 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ]
Mar 26 17:55:00 charon 13[CFG] <2> looking for an IKEv2 config for IP PUBLIQUE WAN PFSENSE...IP PUBLIQUE DU CLIENT
Mar 26 17:55:00 charon 13[CFG] <2> candidate: %any...%any, prio 24
Mar 26 17:55:00 charon 13[CFG] <2> candidate: IP PUBLIQUE WAN PFSENSE...%any, prio 1052
Mar 26 17:55:00 charon 13[CFG] <2> found matching ike config: IP PUBLIQUE WAN PFSENSE...%any with prio 1052
Mar 26 17:55:00 charon 13[IKE] <2> received MS NT5 ISAKMPOAKLEY v9 vendor ID
Mar 26 17:55:00 charon 13[IKE] <2> received MS-Negotiation Discovery Capable vendor ID
Mar 26 17:55:00 charon 13[IKE] <2> received Vid-Initial-Contact vendor ID
Mar 26 17:55:00 charon 13[ENC] <2> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02
Mar 26 17:55:00 charon 13[IKE] <2> IP PUBLIQUE DU CLIENT is initiating an IKE_SA
Mar 26 17:55:00 charon 13[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> no acceptable INTEGRITY_ALGORITHM found
Mar 26 17:55:00 charon 13[CFG] <2> selecting proposal:
Mar 26 17:55:00 charon 13[CFG] <2> proposal matches
Mar 26 17:55:00 charon 13[CFG] <2> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_192/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_192/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_192/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA1/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_128/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA1/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_256/PR
Mar 26 17:55:00 charon 13[CFG] <2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Mar 26 17:55:00 charon 13[CFG] <2> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Mar 26 17:55:00 charon 13[IKE] <2> remote host is behind NAT
Mar 26 17:55:00 charon 13[IKE] <2> sending cert request for "CN=vpnca, C=FR, L=Montelimar, O=Gentlemen du demenagement, OU=Gentlemen du demenagement"
Mar 26 17:55:00 charon 13[ENC] <2> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ]
Mar 26 17:55:00 charon 13[NET] <2> sending packet: from IP PUBLIQUE WAN PFSENSE[500] to IP PUBLIQUE DU CLIENT[1038] (345 bytes)
Mar 26 17:55:00 charon 13[NET] <2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (580 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_AUTH request 1 [ EF(1/4) ]
Mar 26 17:55:00 charon 13[ENC] <2> received fragment #1 of 4, waiting for complete IKE message
Mar 26 17:55:00 charon 13[NET] <2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (580 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_AUTH request 1 [ EF(2/4) ]
Mar 26 17:55:00 charon 13[ENC] <2> received fragment #2 of 4, waiting for complete IKE message
Mar 26 17:55:00 charon 13[NET] <2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (580 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_AUTH request 1 [ EF(3/4) ]
Mar 26 17:55:00 charon 13[ENC] <2> received fragment #3 of 4, waiting for complete IKE message
Mar 26 17:55:00 charon 13[NET] <2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (212 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_AUTH request 1 [ EF(4/4) ]
Mar 26 17:55:00 charon 13[ENC] <2> received fragment #4 of 4, reassembled fragmented IKE message (1696 bytes)
Mar 26 17:55:00 charon 13[ENC] <2> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ]
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid ee:6a:0f:1d:67:94:cf:44:ff:cf:1b:a8:e2:f2:68:50:86:6d:15:f8
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 0d:90:5d:fb:98:91:6d:02:5b:f6:58:d0:3b:f8:2c:3c:1f:39:9e:fd
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88💿3b:15
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for "CN=vpnca, C=FR, L=Montelimar, O=Gentlemen du demenagement, OU=Gentlemen du demenagement"
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 61:7d:5a:ba:9b:26:ec:87:20:b5:29:1c:a6:4b:06:c6:05:f6:30:2a
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 4d:e4:5d:d6:72:f2:d7:91:10:ae:a2:e2:1b:fe:0f:d7:b2:79:d9:f3
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid f9:27:b6:1b:0a:37:f3:c3:1a:fa:17:ec:2d:46:17:16:12:9d:0c:0e
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 7c:32:d4:85:fd:89:0a:66:b5:97:ce:86:f4:d5:26:a9:21:07:e8:3e
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 64:1d:f8:d5:0e:23:31:c2:29:b2:50:cb:32:f5:6d:f5:5c:8e:00:fa
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid da:ed:64:74:14:9c:14:3c:ab:dd:99:a9:bd:5b:28:4d:8b:3c:c9:d8
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 5e:8c:53:18:22:60:1d:56:71:d6:6a:a0:cc:64:a0:60:07:43:d5:a8
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 86:26:cb:1b:c5:54:b3:9f:bd:6b:ed:63:7f:b9:89:a9:80:f1:f4:8a
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid b5:99:33:43:ac:a2:17:c5:08:ba:88:8c:a6:92:7e:26:b3:0f:87:a9
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid f7:93:19:ef:df:c1:f5:20:fb:ac:85:55:2c:f2:d2:8f:5a:b9:ca:0b
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid c4:30:28:c5:d3:e3:08:0c:10:44:8b:2c:77:ba:24:53:97:60:bb:f9
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid a2:af:24:0a:da:e8:67:79:c8:a8:50:b3:c7:46:ee:d9:f7:1b:16:78
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid f8:16:51:3c:fd:1b:44:9f:2e:6b:28:a1:97:22:1f:b8:1f:51:4e:3c
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 73:97:82:ea:b4:04:16:6e:25:d4:82:3c:37:db:f8:a8:12:fb:cf:26
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 69:9f:1b:7a:e9:b8:da:18:49:6c:60:8b:ce:4f:4e:aa:f9:f0:b7:aa
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid ba:42:b0:81:88:53:88:1d:86:63:bd:4c:c0:5e:08:fe:ea:6e:bb:77
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid c5:30:21:e4:c8:4b:d1:a9:e9:e8:40:ba:6a:16:9f:77:92:8f:91
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 6e:58:4e:33:75:bd:57:f6:d5:42:1b:16:01:c2:d8:c0:f5:3a:9f:6e
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 4a:81:0c:f0:c0:90:0f:19:06:42:31:35:a2:a2:8d:d3:44:fd:08
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 6c:ca:bd:7d:b4:7e:94:a5:75:99:01:b6:a7:df:d4:5d:1c:09:1c:cc
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 42:32:b6:16:fa:04:fd:fe:5d:4b:7a:c3:fd:f7:4c:40:1d:5a:43:af
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid a5:06:8a:78:cf:84:bd:74:32:dd:58:f9:65:eb:3a:55:e7:c7:80:dc
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 6d:aa:9b:09:87:c4:d0:d4:22:ed:40:07:37:4d:19:f1:91:ff:d3
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 7e:95:9f:ed:82:8e:2a:ed:c3:7c:0d:05:46:31:ef:53:97:48:49
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 3e:51:59:8b:a7:6f:54:5c:77:24:c5:66:eb:aa:fb:3e:2b:f3:ac:4f
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid fd:da:14:c4:9f:30:de:21:bd:1e:42:39:fc:63:23:49:e0:f1:84
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 3e:22:d4:2c:1f:02:44:b8:04:10:65:61:7c:c7:6b:ae:da:87:29:9c
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 55:e4:81:d1:11:80:be:d8:89:b9:08:a3:31:f9:a1:24:09:16:b9:70
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 21:0f:2c:89:f7:c4:cd:5d:1b:82:5e:38:d6:c6:59:3b:a6:93:75:ae
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid e9:f1:a5:63:62:fb:f3:d3:51:12:11:b1:ae:9c:65:03:94:9e:c5:22
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid c4:52:72:20:a9:58:c0:6e:9d:4b:f2:0b:21:12:3c:eb:3a:0b:6b:6f
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid c4:52:72:20:a9:58:c0:6e:9d:4b:f2:0b:21:12:3c:eb:3a:0b:6b:6f
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 23:0c:95:01:34:a6:1c:7a:6f:79:4a:ea:f3:61:7b:fc:b1:d1:0d:7a
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 67:ec:9f:90:2d:64:ae:fe:7e:bc:f8:8c:51:28:f1:93:2c:12
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 17:4a:b8:2b:5f:fb:05:67:75:27:ad:49:5a:4a:5d:c4:22:cc:ea:4e
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid ee:6a:0f:1d:67:94:cf:44:ff:cf:1b:a8:e2:f2:68:50:86:6d:15:f8
Mar 26 17:55:00 charon 13[IKE] <2> received cert request for unknown ca with keyid b3:d3:ff:d9:0c:62:06:45:72:b3:1d:42:fb:61:a6:79:c5:8c:cd:03
Mar 26 17:55:00 charon 13[IKE] <2> received 61 cert requests for an unknown ca
Mar 26 17:55:00 charon 13[CFG] <2> looking for peer configs matching IP PUBLIQUE WAN PFSENSE[%any]...IP PUBLIQUE DU CLIENT[192.168.1.30]
Mar 26 17:55:00 charon 13[CFG] <2> candidate "bypasslan", match: 1/1/24 (me/other/ike)
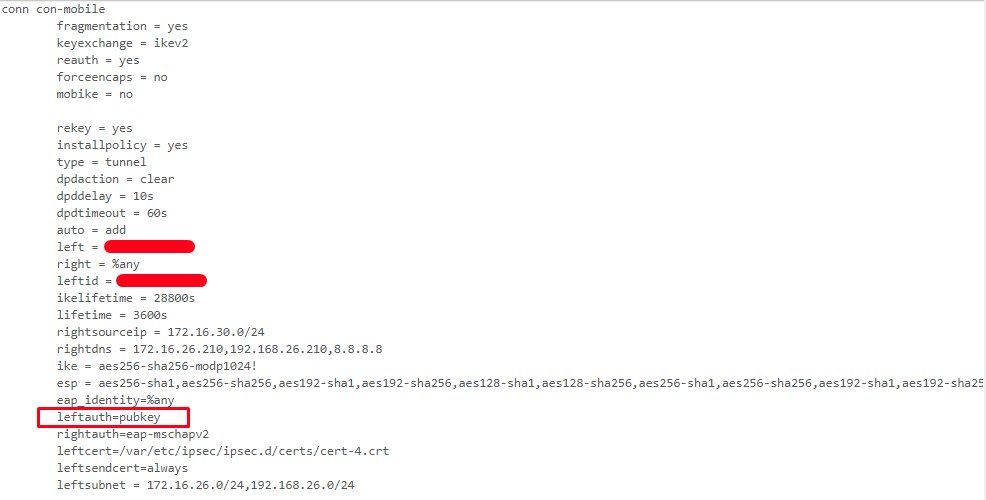
Mar 26 17:55:00 charon 13[CFG] <2> candidate "con-mobile", match: 1/1/1052 (me/other/ike)
Mar 26 17:55:00 charon 13[CFG] <2> ignore candidate 'bypasslan' without matching IKE proposal
Mar 26 17:55:00 charon 13[CFG] <con-mobile|2> selected peer config 'con-mobile'
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> initiating EAP_IDENTITY method (id 0x00)
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP4_ADDRESS attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP4_DNS attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP4_NBNS attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP4_SERVER attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP6_ADDRESS attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP6_DNS attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> processing INTERNAL_IP6_SERVER attribute
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> peer supports MOBIKE, but disabled in config
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> authentication of 'IP PUBLIQUE WAN PFSENSE' (myself) with RSA signature successful
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> sending end entity cert "CN=PfsenseMASTER_OVH.lgdd.local, C=FR, L=Montelimar, O=Gentlemen du demenagement, OU=Gentlemen du demenagement"
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> splitting IKE message (1648 bytes) into 2 fragments
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> generating IKE_AUTH response 1 [ EF(1/2) ]
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> generating IKE_AUTH response 1 [ EF(2/2) ]
Mar 26 17:55:00 charon 13[NET] <con-mobile|2> sending packet: from IP PUBLIQUE WAN PFSENSE[4500] to IP PUBLIQUE DU CLIENT[4500] (1236 bytes)
Mar 26 17:55:00 charon 13[NET] <con-mobile|2> sending packet: from IP PUBLIQUE WAN PFSENSE[4500] to IP PUBLIQUE DU CLIENT[4500] (484 bytes)
Mar 26 17:55:00 charon 13[NET] <con-mobile|2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (96 bytes)
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> parsed IKE_AUTH request 2 [ EAP/RES/ID ]
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> received EAP identity 'LGDD\m.blainville'
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> initiating EAP_MSCHAPV2 method (id 0x7F)
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> generating IKE_AUTH response 2 [ EAP/REQ/MSCHAPV2 ]
Mar 26 17:55:00 charon 13[NET] <con-mobile|2> sending packet: from IP PUBLIQUE WAN PFSENSE[4500] to IP PUBLIQUE DU CLIENT[4500] (112 bytes)
Mar 26 17:55:00 charon 13[NET] <con-mobile|2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (160 bytes)
Mar 26 17:55:00 charon 13[ENC] <con-mobile|2> parsed IKE_AUTH request 3 [ EAP/RES/MSCHAPV2 ]
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> no EAP key found for hosts 'IP PUBLIQUE WAN PFSENSE' - 'LGDD\m.blainville'
Mar 26 17:55:00 charon 13[IKE] <con-mobile|2> EAP-MS-CHAPv2 verification failed, retry (1)
Mar 26 17:55:01 charon 12[MGR] ignoring request with ID 3, already processing
Mar 26 17:55:02 charon 12[MGR] ignoring request with ID 3, already processing
Mar 26 17:55:02 charon 13[ENC] <con-mobile|2> generating IKE_AUTH response 3 [ EAP/REQ/MSCHAPV2 ]
Mar 26 17:55:02 charon 13[NET] <con-mobile|2> sending packet: from IP PUBLIQUE WAN PFSENSE[4500] to IP PUBLIQUE DU CLIENT[4500] (128 bytes)
Mar 26 17:55:04 charon 12[NET] <con-mobile|2> received packet: from IP PUBLIQUE DU CLIENT[4500] to IP PUBLIQUE WAN PFSENSE[4500] (80 bytes)
Mar 26 17:55:04 charon 12[ENC] <con-mobile|2> DELETE verification failed
Mar 26 17:55:04 charon 12[ENC] <con-mobile|2> could not decrypt payloads
Mar 26 17:55:04 charon 12[IKE] <con-mobile|2> message verification failedPlease also mark the comments that contributed to the solution of the article
Content-Key: 561379
Url: https://administrator.de/contentid/561379
Printed on: April 26, 2024 at 01:04 o'clock
3 Comments
Latest comment
IPsec is a suite of protocols for securing network connections, but the details and many variations quickly become overwhelming. Unfortunately if you just need a simple IPsec setup for a small number of hosts (e.g. less than 10) this is exactly the kind of complexity that you might end up dealing with anyway. What I'm going to show you here is not so much a recipe, but more a collection of recipes that might give you some more sensible choices when setting up an IPsec VPN for your infrastructure, and should hopefully save you some time in the process too.